
Emotet banking Trojan attack in 2022 | Cyber Security | VARINDIA News Hour
The actor behind Emotet is a hacker group known as Mealybug. Since starting in 2014 with the first and simplest version of the Trojan, they have turned their operation into a successful crimeware rink that provides Malware-as-a-Service (MaaS). The group achieved this by creating a botnet of infected computers on Emotet malware infrastructure, which they then sold access to. The botnet runs from three clusters of servers known as Epoch 1, Epoch 2, and Epoch 3. They rented this framework to various ransomware ventures, including the infamous Ryuk gang. The distribution mechanism of Emotet is through malspam. Emotet ransacks your contacts list and sends itself to your friends, family, coworkers and clients. Since these emails are coming from your hijacked email account, the emails look less like spam and the recipients, feeling safe, are more inclined to click bad URLs and download infected files. If a connected network is present, Emotet spreads using a list of common passwords, guessing its way onto other connected systems in a brute-force attack. If the password to the all-important human resources server is simply “password” then it’s likely Emotet will find its way there.
Emotet continues to be among the most costly and destructive malware affecting SLTT governments. Its worm-like features result in rapidly spreading network-wide infection, which are difficult to combat. Emotet infections have cost SLTT governments up to $1 million per incident to remediate. Emotet malware infiltrates computers through a network spreader component which consists of several spreader modules. The infrastructure that was used by EMOTET involved several hundreds of servers located across the world, all of these having different functionalities in order to manage the computers of the infected victims, to spread to new ones, to serve other criminal groups, and to ultimately make the network mor
By VARINDIA| 21 views

The Growing Trickbot Attacks | Trickbot Malware | Posing Concerns | VARINDIA News Hour
TrickBot attack, the Windows services and the activities of Windows Defender or other antivirus software are first terminated. Various methods are then used to extend privileges. The cybercrime operators behind the infamous TrickBot malware have as soon as once more upped the ante by fine-tuning its strategies by including a number of layers of protection to slide previous anti-malware merchandise. The resulting administrative rights can then be used by further plug-ins, which the malware loads automatically. Subsequently, TrickBot spies on both the system and the networks and collects data from the user. The information gathered by the malware is then forwarded to external devices, or to the cybercriminals behind the attack. As per Kaspersky, initially, TrickBot often found its way into the system through phishing emails. This involves sending deceptively genuine fake emails from well-known institutions and companies, which often have an attachment. Victims of a TrickBot attack are requested in the email to open the attachment or link, which leads to the infection of the device. Opening the attachments causes the malware to be downloaded. A TrickBot infection can also occur, through malicious updates or through malware that is already on the end device. Once the malware has made it onto the computer and is able to save the user's data, one of its main goals is to remain undetected for as long as possible.
A Research on Trickbot says, the malware targeting companies in retail, building materials, manufacturing, insurance, and construction with phishing emails are designed to steal credentials. The Trickbot malware is designed to build a botnet—a network of hundreds or sometimes thousands of hacked and connected devices used to launch attacks on organizations and individuals. Russian-based criminals behind the notorious malware known as Trickbot appear to b
By VARINDIA| 24 views

Digital Currency Glitches | Global Concerns | VARINDIA News Hour
The ambiguities surrounding the digital currency still leave enough space for the analysis of its unreserved acceptance, trust and anticipation, which are the main drivers for the spread of the network. It is time for the Banks to carefully consider the technology underlying these cryptocurrencies as a potential generic new way of transferring ownership of the value over the long term. Especially Bitcoin is the technology adoption in the presence of network externalities. The growth in digital currencies could make cross-border payments more efficient and help address the $1.7 trillion global trade financing gap. These burgeoning currencies may not solve all trade issues, however, and could further complicate the supply and demand of foreign exchange, especially for countries with limited existing international trade. There is no doubt that the digital currencies are growing: the market is valued at more than $2 trillion and involves more than 15,000 varieties. Based on the Atlantic Council’s CBDC tracker, nine countries or currency unions have launched their digital currencies, while 15 are in the pilot phase. Additionally, 16, including India, are in the development stage, and 40 are in the research stage. Seven are inactive and two have cancelled any plans to launch it.
Digital currencies could provide alternative credit information for trade finance and there’s a $1.7 trillion global trade financing gap, which heavily impacts SMEs who typically don’t have established financial records with banks. Public ledgers of digital currencies could be used to share payment and financial history to underwrite loans for import and export. At the same time, strong privacy protocols would need to be enforced in order to achieve this. The Reserve Bank of India will launch the CBDC from the upcoming financial year. This follows the government’s plans to launch the CBDC that will be backed by bloc
By VARINDIA| 17 views

Increasing social engineering attacks - Smishing, vishing, and phishing | VARINDIA News Hour
We live in a world that’s becoming more digitally dependent. Right from our social interactions to professional interchanges and financial transactions, most take place digitally. Smishing and vishing are two types of fraud that use SMS (smishing) and voice (vishing) to trick people into giving up money or personal information. They’re “social engineering attacks,” meaning that in a smishing or vishing attack, the attacker uses impersonation to exploit the target’s trust. Because 96% of phishing attacks arrive via email, the term “phishing” is sometimes used to refer exclusively to email-based attacks. A recent survey revealed some alarming numbers about Indian companies managing personal identifiable data and electronic health records. While digital resources are enabling, they also leave us vulnerable to cyber criminals as a lot of information regarding our personal and professional lives rests in the digital domain. Cyber insurance or cyber security insurance provides coverage from activities such as identity theft, unauthorized transactions, and more. Buying a cyber insurance policy can safeguard against online frauds. The policy can be bought by anyone who is 18 years and above and can be bought for family members. Nearly 58% of Indian companies have not opted for cyber insurance yet, indicating lack of awareness about cyber-attacks and cyber risk management strategies. The survey by RIMS and JB Boda Group says, as more attacks on utilities and industrial systems emerge, with Ransomware involved, it no longer is an IT related issue, but of the CFO and board.
The COVID-19 pandemic has triggered digital transformation across companies, leading to the creation of a complex IT landscape in the form of public clouds, unfamiliar home networks, external systems connected through APIs, along with a plethora of access points into their sphere of monitoring and
By VARINDIA| 18 views

It is true that increasing #cloudcomplexity can lead to cloud repatriation, which is the process of moving workloads and data from the cloud back to on-premises data centers or other private infrastructure.
Many senior IT leaders struggle with increasing cloud complexity. As organizations adopt more cloud technologies and services, managing and securing their cloud infrastructure can become increasingly challenging. A survey conducted by Dynatrace found that 98% of senior IT leaders reported experiencing cloud-related issues, with 78% of them stating that cloud complexity was their top challenge.
The complexity of cloud environments can arise due to a variety of factors, including multiple cloud service providers, a mix of public and private clouds, and the need to integrate with on-premises infrastructure. This complexity can lead to issues such as security vulnerabilities, data loss, and compliance risks. This will further lead to challenges such as vendor lock-in, data sovereignty concerns, and compliance issues, among others.
Today's Headline in NewsHours
0:00 Intro
2:46 #Twitter to verify the top 10,000 most-followed firms for free
3:17 Italy expresses concern over ChatGPT breaching EU’s GDPR clauses
3:55 #Amazon may get sued for gathering kids' data via Alexa
4:30 Parliamentary panel expresses concern over delay in data protection bill
5:00 Fans complain of Jio Cinema app crashing on IPL opening day
Follow Us On :-
Website:https://varindia.com/
https://www.facebook.com/VARINDIAMagazine/
https://twitter.com/varindiamag
https://www.instagram.com/varindia/
https://www.linkedin.com/company/14636899/admin/
https://in.pinterest.com/varindia/
https://varindia.tumblr.com/
Visit on https://varindia.com/ to know more
Labels & Copyrights :- VARINDIA
#CloudRepatriation, #IncreasedComplexity, #C
By VARINDIA| 24 views

Need to strategize and address the growing | Multi-Cloud Networking Challenges | VARINDIA News Hour
To keep pace with growing user expectations around digital experiences while honouring data privacy and residency regulations, more and more applications are being decomposed and distributed across different cloud platforms. For NetOps and DevOps practitioners, this creates a need for simplifying app-to-app networking across multiple clouds as a foundation for distributing applications. Over 90% of enterprises are embracing a multi-cloud strategy. Simply put, a multi-cloud approach offers significant advantages to organizations seeking to optimize the Three Cs of Cloud: Cost, Capabilities and Compliance. Still, with all the advantages to be gained with a multi-cloud approach, executives should be aware of the downsides. It is time to address multi-cloud networking and distributed cloud services that can seamlessly integrate into your existing infrastructure and provide immediate value-add for existing and new applications to deliver, secure, and interconnect apps in multiple clouds without being an expert in each one by leveraging automation to build app-to-app networking and security policies across multiple clouds. The challenge in multi-cloud adoption is managing complexity, the more cloud environments your organization uses, the more complex the management task becomes. The problem lies in the diversity among cloud vendors. Each public cloud vendor has its own portal, its own APIs, and its own unique processes for managing its environment. Because there is no standardization across public cloud vendors, multiplying vendors means multiplying the management burden.
However, the advantage is from the side of cost control. Multi-cloud is the ability to provide developers and database administrators with a “self-service” experience, that is, the ability to quickly deploy their applications in their cloud environment of choice. Unfortunately, this can
By VARINDIA| 18 views

Safety of CBDC from vulnerability and cyber attacks | VARINDIA explained | VARINDIA News Hour
#CBDC is a digital form of central bank money that can be accessible to the general public; essentially, it consists of individuals and firms having access to transaction and savings accounts with their home country’s central bank. The Government of India has proposed to issue CBDC, ‘Digital Rupee’ during the FY2022-23 which would be a digital avatar of India’s Fiat Currency, controlled and monitored by the Reserve Bank of India (RBI). CBDC will be a legal tender, being a revamped version of the physical currency, which will eventually reduce cost of currency management. CBDC could help policy-makers achieve goals around payment efficiency, financial inclusion, banking and payment competitiveness, access to safe central bank money in the era of digital payments, and more. People can convert digital currency to physical currency and vice-versa with ease. As per RBI, the digital rupee blockchain being developed by the RBI would be able to trace all transactions, unlike the current system of mobile wallets offered by private companies. The units issued in the digital rupee would be included in the currency in circulation, it added. The RBI's digital currency is likely to debut by early 2023. Currently, the bitcoin blockchain supports up to seven transactions per second and then there are some others that let a few thousand transactions per second. However, security aspects involved in constructing and deploying a central bank digital currency (CBDC).
It is a matter of great concern on the Security part, which is an essential element in the CBDC system. In addition to securing the underlying storage and transfer of value, security involves
aspects of privacy and resilience. Threats must be mitigated to protect the integrity of funds and the confidentiality of users. A secure CBDC system will retain public trust in the central bank. Under an ac
By VARINDIA| 22 views

Data Breaching | Cyber Insurance Opportunities | VARINDIA News Hour
We live in a world that’s becoming more digitally dependent. Right from our social interactions to professional interchanges and financial transactions, most take place digitally. While digital resources are enabling, they also leave us vulnerable to cyber criminals as a lot of information regarding our personal and professional lives rests in the digital domain. Cyber insurance or cyber security insurance provides coverage from activities such as identity theft, unauthorized transactions, and more with rapidly increasing digitalisation, cyber risks and loss scenarios keep changing quickly. For all risk owners this makes it even more important to learn from past incidents and identify upcoming cybersecurity trends, threats and vulnerabilities. Cyber insurers have already proven that they can be part of the solution when it comes to building up resiliency and preparedness across all industries. The total global economic damage of cybercrime is a controversial issue. Cybersecurity Ventures estimates global economic cybercrime costs to grow by 15% per year over the next five years, reaching $10.5 trillion annually by 2025. In 2021, the number is expected to be $6 trillion up from $3 trillion in 2015. This is no surprise as the cybercriminal world is advancing at a fast pace.
Having cyber insurance is a good idea if the costs make sense — it could be the difference between going out of business and staying afloat. Even if you can afford and qualify for coverage, you should know that cybercriminals like to attack companies with cyber insurance. According to a recent survey, these organizations are over two times more likely to pay ransoms than those without it. Hackers even find out the value of potential victims' coverage by breaking into the insurance companies first so they can demand the highest possible ransom. Once they've extorted organizations with cyber insurance, the
By VARINDIA| 21 views
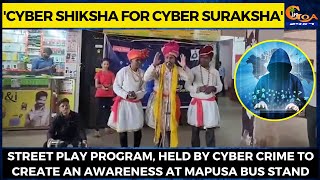
'Cyber Shiksha for Cyber Suraksha' Street play program, held by cyber crime to create an awareness at Mapusa bus stand
#Goa #GoaNews #streetplay #Cyber #crime #awareness #Mapusa
'Cyber Shiksha for Cyber Suraksha' Street play program, held by cyber crime to create an awareness
By ingoanews| 26 views
Increasing Concerns On Cloud Services Are Under Attack | Cyber Attack | VARINDIA News Hour
With the new hybrid-working model we see organizations increasingly moving more of their workload settings to the cloud. While this transformation offers great agility and scalability benefits, it comes with inherent and increased risks to security and compliance. A simple configuration error can result in your entire organization being exposed to threat actors who no longer need to break into your data center to access your critical data or conduct ransomware attacks. As per Gartner by 2025, 99% of cloud security issues will be a result of human error when configuring assets and security in the cloud. At a time when organizations are becoming increasingly dependent on third-party cloud vendors such as AWS, Microsoft Azure, IBM and Google Cloud Platform to securely manage their data, concerns around misconfigurations and other vulnerabilities in the cloud are likely to amplify quickly. What’s more, many of the organizations finding themselves at risk have had to accelerate their digital transformation initiatives at an uncomfortable pace over the past two years, resulting in knowledge and talent gaps that only add to their fears around cloud security.
Under the shared responsibility model - a security framework designed to ensure accountability for compromised data and other incidents - the cloud provider will offer basic cloud security, but it's up to businesses themselves to secure their own data within the cloud. To put it in another way, if cloud providers ensure the town gates are locked and the perimeter is well guarded, it’s still up to businesses to ensure their own doors are locked. That’s no mean feat, particularly when you consider that many large enterprises now rely on three or four cloud platforms as part of a multi-cloud strategy. Attacks on cloud service providers are ramping up. As outlined in Check Point 2022 Security Report, the previo
#FACEBOOK#amazon#russia#indianrailways#Microsoft#tutorial#Paypal#AWS#MicrosoftAzure#Varindia#GoogleCloud#Digitalocean#cloudcomputingexplained#OneWeb#ashwanivaishnaw#RailwayMinisterAshwiniVaishnaw#varindianewshour#Cloudsecurity#Azure#hybridworking#CloudServicesUnderAttack#IBMandGoogleCloudPlatform#CSSTricks#GMPCSlicence#Bhartigroup#Instagramban#cloudprovider#whatarecloudservices#typesofcloudcomputingservices#basicofcloudcomputing

Best Mobile Processors Explained in Telugu
Join Telegram : https://telegram.me/telugutechtuts
#telugutechtuts #mobileprocessor #snapdragon #exynos #mediatek #applebionic
ICICI Demat: earn money: https://bit.ly/3f80pRG
Demat account in telugu zerodha : http://bit.ly/2YlutyX
Earn money with upstox : https://bit.ly/3dsiUL6
Earn money With ANGEL BROKING :http://bit.ly/2GbdyUO
Get in Touch With Me :
Follow me on Fb: https://www.facebook.com/telugutechtutsofficial
Follow me on Twitter : https://twitter.com/hafizsd
Follow Me on Instagram: https://www.instagram.com/telugutechtuts/
ఏ Processor మంచిది ? || Best Mobile Processors Explained in Telugu
By Telugu TechTuts| 0 views

#mobilebuyingguide #gadgets #gamingmobile
Join Telegram : https://telegram.me/telugutechtuts
ICICI Demat: earn money: https://bit.ly/3f80pRG
Demat account in telugu zerodha : http://bit.ly/2YlutyX
Earn money with upstox : https://bit.ly/3dsiUL6
Earn money With ANGEL BROKING :http://bit.ly/2GbdyUO
Get in Touch With Me :
Follow me on Fb: https://www.facebook.com/telugutechtutsofficial
Follow me on Twitter : https://twitter.com/hafizsd
Follow Me on Instagram: https://www.instagram.com/telugutechtuts/
Gaming Mobile కొనే ముందు ఈ వీడియో చూడండి ???? || Telugu Tech Tuts
By Telugu TechTuts| 0 views

15 వేలకి దగ్గర్లో ఏ మొబైల్ కొనాలి ?
Join Telegram : https://telegram.me/telugutechtuts
#mobilebuyingguide #gadgets #telugutechtuts
ICICI Demat: earn money: https://bit.ly/3f80pRG
Demat account in telugu zerodha : http://bit.ly/2YlutyX
Earn money with upstox : https://bit.ly/3dsiUL6
Earn money With ANGEL BROKING :http://bit.ly/2GbdyUO
Get in Touch With Me :
Follow me on Fb: https://www.facebook.com/telugutechtutsofficial
Follow me on Twitter : https://twitter.com/hafizsd
Follow Me on Instagram: https://www.instagram.com/telugutechtuts/
Best Mobiles to Buy Under 15,000 in February 2024 || Telugu Tech Tuts
By Telugu TechTuts| 0 views

#DYK India is the largest #Software exporter in the world? As India completes #75yearsofIndependence, let's look at the country's IT journey over the last 75yrs.
#IndiaAt75 #HarGharTiranga #AmritMahotsav #CIICelebratesIndiaat75
CII Celebrates India@75 - India's IT Journey@75
By CII| 226558 views

Launch of Gujarat Election Campaign in Ahmedabad.
#CongressNuKaamBoleChe
Declaration:
This video is an intellectual property belonging to the Indian National Congress. Please seek prior permission before using any part of this video in any form.
For more videos, subscribe to Congress Party channel: https://www.youtube.com/user/indiacongress
Follow Indian National Congress!
Follow the Indian National Congress on
Facebook: https://www.facebook.com/IndianNationalCongress
Twitter:https://twitter.com/INCIndia
Instagram: https://www.instagram.com/incindia/
YouTube: https://www.youtube.com/user/indiacongress
Follow Rahul Gandhi on
YouTube: https://www.youtube.com/c/rahulgandhi/
Facebook: https://www.facebook.com/rahulgandhi/
Twitter: https://twitter.com/rahulgandhi/
Instagram: https://www.instagram.com/rahulgandhi/
Launch of Gujarat Election Campaign in Ahmedabad
By Indian National Congress| 170472 views

Education ???? पर Arvind Kejriwal की जबरदस्त Speech ???? | Latest Motivational Speech | Aam Aadmi Party
#arvindkejriwal #education #aamaadmiparty
Arvind Kejriwal All Interviews:
https://youtube.com/playlist?list=PLiN7YZXz4nOc23gNiOivcdgeYUEpUUqlU
Arvind Kejriwal All Townhalls:
https://youtube.com/playlist?list=PLiN7YZXz4nOdQ-o4kATbxyeNHjD1SyT8n
Arvind Kejriwal in Punjab Series:
https://youtube.com/playlist?list=PLiN7YZXz4nOcJRxl8iqYDKsL26FKUvmSr
Arvind Kejriwal in Goa Series:
https://youtube.com/playlist?list=PLiN7YZXz4nOflmK5x_tdfrryxrSc3SBzm
Arvind Kejriwal In Uttarakhand Series:
https://youtube.com/playlist?list=PLiN7YZXz4nOcZ5TuqFQsJUmwRdNwvKsCT
Arvind Kejriwal on Baba Saheb Ambedkar:
https://youtube.com/playlist?list=PLiN7YZXz4nOfWtKqvMU22KihHk2jiUXdS
Follow Arvind Kejriwal on Social Media :
Follow Arvind Kejriwal on Twitter: https://www.twitter.com/ArvindKejriwal
Follow Arvind Kejriwal on Facebook: https://www.facebook.com/AAPkaArvind/
Follow Aam Aadmi Party on Facebook: https://www.facebook.com/AamAadmiParty
Follow Aam Aadmi Party on Twitter: https://www.twitter.com/AamAamAadmiParty
Education ???? पर Arvind Kejriwal की जबरदस्त Speech ???? | Latest Motivational Speech | Aam Aadmi Party
By AAP| 209312 views

Here is my interview with Shri Sudhir Raval on Jan Man India Channel.
Watch My interview with Jan Man India With HD Quality
By Mansukh Mandaviya| 819321 views

Prime Minister Narendra Modi
---------------------------------------------------------------------------
►Subscribe https://goo.gl/C3hVED | to Prime Minister Office’s official Youtube channel.
Get the latest updates ???? from PM’s Office: news, speeches, public outreach, national events, official state visits, PM’s foreign visits, and much more...
You can also connect with us on the official PMO website & other Social Media channels –
►Website – http://www.pmindia.gov.in
►Facebook – https://www.facebook.com/PMOIndia
►Twitter – https://twitter.com/PMOIndia
►Instagram – https://www.instagram.com/pmoindia
India observes Independence Day with patriotic fervour
By PMOfficeIndia| 248620 views

Global Summit 2020 "Mission 5 Trillion – CMA as a Cryogenic Force"
Watch Technical Session V, Q&A With HD Quality
By ICMAI| 898581 views

Emotet banking Trojan attack in 2022 | Cyber Security | VARINDIA News Hour
The actor behind Emotet is a hacker group known as Mealybug. Since starting in 2014 with the first and simplest version of the Trojan, they have turned their operation into a successful crimeware rink that provides Malware-as-a-Service (MaaS). The group achieved this by creating a botnet of infected computers on Emotet malware infrastructure, which they then sold access to. The botnet runs from three clusters of servers known as Epoch 1, Epoch 2, and Epoch 3. They rented this framework to various ransomware ventures, including the infamous Ryuk gang. The distribution mechanism of Emotet is through malspam. Emotet ransacks your contacts list and sends itself to your friends, family, coworkers and clients. Since these emails are coming from your hijacked email account, the emails look less like spam and the recipients, feeling safe, are more inclined to click bad URLs and download infected files. If a connected network is present, Emotet spreads using a list of common passwords, guessing its way onto other connected systems in a brute-force attack. If the password to the all-important human resources server is simply “password” then it’s likely Emotet will find its way there.
Emotet continues to be among the most costly and destructive malware affecting SLTT governments. Its worm-like features result in rapidly spreading network-wide infection, which are difficult to combat. Emotet infections have cost SLTT governments up to $1 million per incident to remediate. Emotet malware infiltrates computers through a network spreader component which consists of several spreader modules. The infrastructure that was used by EMOTET involved several hundreds of servers located across the world, all of these having different functionalities in order to manage the computers of the infected victims, to spread to new ones, to serve other criminal groups, and to ultimately make the network mor
By VARINDIA| 21 views

The Growing Trickbot Attacks | Trickbot Malware | Posing Concerns | VARINDIA News Hour
TrickBot attack, the Windows services and the activities of Windows Defender or other antivirus software are first terminated. Various methods are then used to extend privileges. The cybercrime operators behind the infamous TrickBot malware have as soon as once more upped the ante by fine-tuning its strategies by including a number of layers of protection to slide previous anti-malware merchandise. The resulting administrative rights can then be used by further plug-ins, which the malware loads automatically. Subsequently, TrickBot spies on both the system and the networks and collects data from the user. The information gathered by the malware is then forwarded to external devices, or to the cybercriminals behind the attack. As per Kaspersky, initially, TrickBot often found its way into the system through phishing emails. This involves sending deceptively genuine fake emails from well-known institutions and companies, which often have an attachment. Victims of a TrickBot attack are requested in the email to open the attachment or link, which leads to the infection of the device. Opening the attachments causes the malware to be downloaded. A TrickBot infection can also occur, through malicious updates or through malware that is already on the end device. Once the malware has made it onto the computer and is able to save the user's data, one of its main goals is to remain undetected for as long as possible.
A Research on Trickbot says, the malware targeting companies in retail, building materials, manufacturing, insurance, and construction with phishing emails are designed to steal credentials. The Trickbot malware is designed to build a botnet—a network of hundreds or sometimes thousands of hacked and connected devices used to launch attacks on organizations and individuals. Russian-based criminals behind the notorious malware known as Trickbot appear to b
By VARINDIA| 24 views

Digital Currency Glitches | Global Concerns | VARINDIA News Hour
The ambiguities surrounding the digital currency still leave enough space for the analysis of its unreserved acceptance, trust and anticipation, which are the main drivers for the spread of the network. It is time for the Banks to carefully consider the technology underlying these cryptocurrencies as a potential generic new way of transferring ownership of the value over the long term. Especially Bitcoin is the technology adoption in the presence of network externalities. The growth in digital currencies could make cross-border payments more efficient and help address the $1.7 trillion global trade financing gap. These burgeoning currencies may not solve all trade issues, however, and could further complicate the supply and demand of foreign exchange, especially for countries with limited existing international trade. There is no doubt that the digital currencies are growing: the market is valued at more than $2 trillion and involves more than 15,000 varieties. Based on the Atlantic Council’s CBDC tracker, nine countries or currency unions have launched their digital currencies, while 15 are in the pilot phase. Additionally, 16, including India, are in the development stage, and 40 are in the research stage. Seven are inactive and two have cancelled any plans to launch it.
Digital currencies could provide alternative credit information for trade finance and there’s a $1.7 trillion global trade financing gap, which heavily impacts SMEs who typically don’t have established financial records with banks. Public ledgers of digital currencies could be used to share payment and financial history to underwrite loans for import and export. At the same time, strong privacy protocols would need to be enforced in order to achieve this. The Reserve Bank of India will launch the CBDC from the upcoming financial year. This follows the government’s plans to launch the CBDC that will be backed by bloc
By VARINDIA| 17 views

Increasing social engineering attacks - Smishing, vishing, and phishing | VARINDIA News Hour
We live in a world that’s becoming more digitally dependent. Right from our social interactions to professional interchanges and financial transactions, most take place digitally. Smishing and vishing are two types of fraud that use SMS (smishing) and voice (vishing) to trick people into giving up money or personal information. They’re “social engineering attacks,” meaning that in a smishing or vishing attack, the attacker uses impersonation to exploit the target’s trust. Because 96% of phishing attacks arrive via email, the term “phishing” is sometimes used to refer exclusively to email-based attacks. A recent survey revealed some alarming numbers about Indian companies managing personal identifiable data and electronic health records. While digital resources are enabling, they also leave us vulnerable to cyber criminals as a lot of information regarding our personal and professional lives rests in the digital domain. Cyber insurance or cyber security insurance provides coverage from activities such as identity theft, unauthorized transactions, and more. Buying a cyber insurance policy can safeguard against online frauds. The policy can be bought by anyone who is 18 years and above and can be bought for family members. Nearly 58% of Indian companies have not opted for cyber insurance yet, indicating lack of awareness about cyber-attacks and cyber risk management strategies. The survey by RIMS and JB Boda Group says, as more attacks on utilities and industrial systems emerge, with Ransomware involved, it no longer is an IT related issue, but of the CFO and board.
The COVID-19 pandemic has triggered digital transformation across companies, leading to the creation of a complex IT landscape in the form of public clouds, unfamiliar home networks, external systems connected through APIs, along with a plethora of access points into their sphere of monitoring and
By VARINDIA| 18 views

It is true that increasing #cloudcomplexity can lead to cloud repatriation, which is the process of moving workloads and data from the cloud back to on-premises data centers or other private infrastructure.
Many senior IT leaders struggle with increasing cloud complexity. As organizations adopt more cloud technologies and services, managing and securing their cloud infrastructure can become increasingly challenging. A survey conducted by Dynatrace found that 98% of senior IT leaders reported experiencing cloud-related issues, with 78% of them stating that cloud complexity was their top challenge.
The complexity of cloud environments can arise due to a variety of factors, including multiple cloud service providers, a mix of public and private clouds, and the need to integrate with on-premises infrastructure. This complexity can lead to issues such as security vulnerabilities, data loss, and compliance risks. This will further lead to challenges such as vendor lock-in, data sovereignty concerns, and compliance issues, among others.
Today's Headline in NewsHours
0:00 Intro
2:46 #Twitter to verify the top 10,000 most-followed firms for free
3:17 Italy expresses concern over ChatGPT breaching EU’s GDPR clauses
3:55 #Amazon may get sued for gathering kids' data via Alexa
4:30 Parliamentary panel expresses concern over delay in data protection bill
5:00 Fans complain of Jio Cinema app crashing on IPL opening day
Follow Us On :-
Website:https://varindia.com/
https://www.facebook.com/VARINDIAMagazine/
https://twitter.com/varindiamag
https://www.instagram.com/varindia/
https://www.linkedin.com/company/14636899/admin/
https://in.pinterest.com/varindia/
https://varindia.tumblr.com/
Visit on https://varindia.com/ to know more
Labels & Copyrights :- VARINDIA
#CloudRepatriation, #IncreasedComplexity, #C
By VARINDIA| 24 views

Need to strategize and address the growing | Multi-Cloud Networking Challenges | VARINDIA News Hour
To keep pace with growing user expectations around digital experiences while honouring data privacy and residency regulations, more and more applications are being decomposed and distributed across different cloud platforms. For NetOps and DevOps practitioners, this creates a need for simplifying app-to-app networking across multiple clouds as a foundation for distributing applications. Over 90% of enterprises are embracing a multi-cloud strategy. Simply put, a multi-cloud approach offers significant advantages to organizations seeking to optimize the Three Cs of Cloud: Cost, Capabilities and Compliance. Still, with all the advantages to be gained with a multi-cloud approach, executives should be aware of the downsides. It is time to address multi-cloud networking and distributed cloud services that can seamlessly integrate into your existing infrastructure and provide immediate value-add for existing and new applications to deliver, secure, and interconnect apps in multiple clouds without being an expert in each one by leveraging automation to build app-to-app networking and security policies across multiple clouds. The challenge in multi-cloud adoption is managing complexity, the more cloud environments your organization uses, the more complex the management task becomes. The problem lies in the diversity among cloud vendors. Each public cloud vendor has its own portal, its own APIs, and its own unique processes for managing its environment. Because there is no standardization across public cloud vendors, multiplying vendors means multiplying the management burden.
However, the advantage is from the side of cost control. Multi-cloud is the ability to provide developers and database administrators with a “self-service” experience, that is, the ability to quickly deploy their applications in their cloud environment of choice. Unfortunately, this can
By VARINDIA| 18 views

Safety of CBDC from vulnerability and cyber attacks | VARINDIA explained | VARINDIA News Hour
#CBDC is a digital form of central bank money that can be accessible to the general public; essentially, it consists of individuals and firms having access to transaction and savings accounts with their home country’s central bank. The Government of India has proposed to issue CBDC, ‘Digital Rupee’ during the FY2022-23 which would be a digital avatar of India’s Fiat Currency, controlled and monitored by the Reserve Bank of India (RBI). CBDC will be a legal tender, being a revamped version of the physical currency, which will eventually reduce cost of currency management. CBDC could help policy-makers achieve goals around payment efficiency, financial inclusion, banking and payment competitiveness, access to safe central bank money in the era of digital payments, and more. People can convert digital currency to physical currency and vice-versa with ease. As per RBI, the digital rupee blockchain being developed by the RBI would be able to trace all transactions, unlike the current system of mobile wallets offered by private companies. The units issued in the digital rupee would be included in the currency in circulation, it added. The RBI's digital currency is likely to debut by early 2023. Currently, the bitcoin blockchain supports up to seven transactions per second and then there are some others that let a few thousand transactions per second. However, security aspects involved in constructing and deploying a central bank digital currency (CBDC).
It is a matter of great concern on the Security part, which is an essential element in the CBDC system. In addition to securing the underlying storage and transfer of value, security involves
aspects of privacy and resilience. Threats must be mitigated to protect the integrity of funds and the confidentiality of users. A secure CBDC system will retain public trust in the central bank. Under an ac
By VARINDIA| 22 views

Data Breaching | Cyber Insurance Opportunities | VARINDIA News Hour
We live in a world that’s becoming more digitally dependent. Right from our social interactions to professional interchanges and financial transactions, most take place digitally. While digital resources are enabling, they also leave us vulnerable to cyber criminals as a lot of information regarding our personal and professional lives rests in the digital domain. Cyber insurance or cyber security insurance provides coverage from activities such as identity theft, unauthorized transactions, and more with rapidly increasing digitalisation, cyber risks and loss scenarios keep changing quickly. For all risk owners this makes it even more important to learn from past incidents and identify upcoming cybersecurity trends, threats and vulnerabilities. Cyber insurers have already proven that they can be part of the solution when it comes to building up resiliency and preparedness across all industries. The total global economic damage of cybercrime is a controversial issue. Cybersecurity Ventures estimates global economic cybercrime costs to grow by 15% per year over the next five years, reaching $10.5 trillion annually by 2025. In 2021, the number is expected to be $6 trillion up from $3 trillion in 2015. This is no surprise as the cybercriminal world is advancing at a fast pace.
Having cyber insurance is a good idea if the costs make sense — it could be the difference between going out of business and staying afloat. Even if you can afford and qualify for coverage, you should know that cybercriminals like to attack companies with cyber insurance. According to a recent survey, these organizations are over two times more likely to pay ransoms than those without it. Hackers even find out the value of potential victims' coverage by breaking into the insurance companies first so they can demand the highest possible ransom. Once they've extorted organizations with cyber insurance, the
By VARINDIA| 21 views

'Cyber Shiksha for Cyber Suraksha' Street play program, held by cyber crime to create an awareness at Mapusa bus stand
#Goa #GoaNews #streetplay #Cyber #crime #awareness #Mapusa
'Cyber Shiksha for Cyber Suraksha' Street play program, held by cyber crime to create an awareness
By ingoanews| 26 views

#shahidkapoor #birthdaycelebration #shahidkapoorwifebirthday #bollywoodnews #shahidkapoorwife #mirakapoor #celebration #photoshared #todaytrendingnews #bollywoodcelebritiesstory #Entertainment #Bollywood #Shahid Kapoor Wished His Wife On Her Birthday #birthdaybash #ishankhatter #mirarajputkapoor #midnightcelebration #todaymatch #breakingnews #entertainmentnews #bollywoodsensation #kareenakapoorkhan #jabwemet #bloodydaddy #kabirsingh #movie #uttarpradesh #maharastra #mumbai #newstoday #kiaraadvani
Follow Us On:
Facebook : https://www.facebook.com/INDIALNV
Twitter : https://twitter.com/india_lnv
Instagram : https://www.instagram.com/lnv_india/
Shahid Kapoor ने Wife को विश किया Birthday :बोले- तुम मेरे दिल की रानी हो, Share कीं तस्वीरें
By LNV India| 500 views

It's time we celebrate ourselves and get high on self-love! Introducing you to Bollywood Bubble's brand new show 'BodyFaming'. A show that talks about loving your body, smashing age-old beauty norms and being comfortable in your own skin. Watch host Rashita Sahni get up close and personal with Bhumi Pednekar, Nawazuddin Siddiqui, Fatima Sana Shaikh, Mona Singh, Sobhita Dhulipala & Dolly Singh about dealing with body-shaming, getting over their inner insecurities and self-doubt and standing by the mantra - 'my body my rules'! Episodes drop every Tuesday at 2 PM only on Bollywood Bubble. Watch out.
#bodyfamingtrailer #bhumipednekar #nawazuddinsiddiqui #fatimasanashaikh
Check out the video to know more.
SUBSCRIBE To Bollywood Bubble:
Click Here ► http://bit.ly/2hjMB6X
Tune into Bollywood Bubble, your one stop destination for all the latest happenings, hot gossips, rumours and exclusive B-Town news...
Also, Visit - https://www.bollywoodbubble.com . One stop Destination for Latest Bollywood Updates.
Like us on Facebook - https://www.facebook.com/BollywoodBubble
Follow us on Twitter - https://twitter.com/bollybubble
Follow us on Instagram - https://www.instagram.com/bollywoodbubble/
Click on the Subscribe Button NOW and Stay Tuned.
BodyFaming Trailer:Bhumi Pednekar, Nawazuddin Siddiqui, Fatima Shaikh, Mona Singh, Sobhita & Dolly S
By Bollywood Bubble| 220 views

Bigg Boss 17 OPENING VOTING Trend | Kaun Hoga Ghar Se Beghar?
#biggboss17 #ishamalviya #samarthjurel
- Stay Tuned For More Bollywood News
☞ Check All Bollywood Latest Update on our Channel
☞ Subscribe to our Channel https://goo.gl/UerBDn
☞ Like us on Facebook https://goo.gl/7Q896J
☞ Follow us on Twitter https://goo.gl/AjQfa4
☞ Circle us on G+ https://goo.gl/57XqjC
☞ Follow us on Instagram https://goo.gl/x48yEy
Bigg Boss 17 OPENING VOTING Trend | Kaun Hoga Ghar Se Beghar?
By Bollywood Spy| 57 views

Bhumi Pednekar recently appeared in the comedy Thank You For Coming and the film invited some extreme reactions from the viewers. While some praised the film for its bold concept, some shamed it for that. In an exclusive conversation with Bollywood Bubble host Akash Bhatnagar, Bhumi spoke about the latter group of people and slammed them for the shaming. She expressed her disappointment towards people who didn’t criticise the film but its intent. The actress discussed the prevalent gender bias and how people never took offence when she was a part of such stories told from a male perspective. She pointed out how Pankaj Tripathi and Akshay Kumar starrer OMG 2 was supported by the same people who shamed her film, when somewhere they dealt with the same subject. Bhumi revealed if not getting any support from women within the industry disappointed her. She highlighted the hypocrisy of the situation that people accept objectification of women but have a problem with them talking about their sexuality. You can watch the entire conversation here.
#BhumiPednekar #BollywoodBubble
Check out the video to know more.
SUBSCRIBE To Bollywood Bubble:
Click Here ► http://bit.ly/2hjMB6X
Tune into Bollywood Bubble, your one stop destination for all the latest happenings, hot gossips, rumours and exclusive B-Town news...
Also, Visit - https://www.bollywoodbubble.com . One stop Destination for Latest Bollywood Updates.
Like us on Facebook - https://www.facebook.com/BollywoodBubble
Follow us on Twitter - https://twitter.com/bollybubble
Follow us on Instagram - https://www.instagram.com/bollywoodbubble/
Click on the Subscribe Button NOW and Stay Tuned.
Bhumi Pednekar on reaction to Thank You For Coming, OMG 2, lack of gender equality, viewer hypocrisy
By Bollywood Bubble| 344 views

Bigg Boss 17 LATEST VOTING Trend | Kaun Hoga Ghar Se Beghar? | Isha, Samarth, Manasvi, Sana, Arun
#biggboss17 #ishamalviya #samarthjurel
- Stay Tuned For More Bollywood News
☞ Check All Bollywood Latest Update on our Channel
☞ Subscribe to our Channel https://goo.gl/UerBDn
☞ Like us on Facebook https://goo.gl/7Q896J
☞ Follow us on Twitter https://goo.gl/AjQfa4
☞ Circle us on G+ https://goo.gl/57XqjC
☞ Follow us on Instagram https://goo.gl/x48yEy
Bigg Boss 17 LATEST VOTING Trend | Kaun Hoga Ghar Se Beghar? | Isha, Samarth, Manasvi, Sana, Arun
By Bollywood Spy| 76 views

Bigg Boss 17 LIVE | Tissue Ko Lekar Isha Ne Samarth Se Kiya Jhagda
#biggboss17 #abhishekkumar #ishamalviya
- Stay Tuned For More Bollywood News
☞ Check All Bollywood Latest Update on our Channel
☞ Subscribe to our Channel https://goo.gl/UerBDn
☞ Like us on Facebook https://goo.gl/7Q896J
☞ Follow us on Twitter https://goo.gl/AjQfa4
☞ Circle us on G+ https://goo.gl/57XqjC
☞ Follow us on Instagram https://goo.gl/x48yEy
Bigg Boss 17 LIVE | Tissue Ko Lekar Isha Ne Samarth Se Kiya Jhagda
By Bollywood Spy| 51 views

On Bigg Boss 17 we have seen the fastest wild card entries and these would only cause lots of fireworks on the show. Now as Samarth Jurel, who is Isha Malviya's boyfriend, enters the BB17 house as a contestant, he spoke to Bollywood Bubble's host Nawaz Kochra. From exposing the violence Abhishek Kumar inflicted on Isha to sharing how Isha's ex used to slap her and cause her harm. He even confirmed their relationship and shared how seeing Isha getting close to Abhishek left him heartbroken. Commenting on Isha being Ankita Lokhande's shadow, Samarth also explained how his entry will change the dynamics on the show. Watch this explosive interview here!
#samarthjurel #ishamalviya #bollywoodbubble
Check out the video to know more.
SUBSCRIBE To Bollywood Bubble:
Click Here ► http://bit.ly/2hjMB6X
Tune into Bollywood Bubble, your one stop destination for all the latest happenings, hot gossips, rumours and exclusive B-Town news...
Also, Visit - https://www.bollywoodbubble.com . One stop Destination for Latest Bollywood Updates.
Like us on Facebook - https://www.facebook.com/BollywoodBubble
Follow us on Twitter - https://twitter.com/bollybubble
Follow us on Instagram - https://www.instagram.com/bollywoodbubble/
Click on the Subscribe Button NOW and Stay Tuned.
Isha Malviya’s boyfriend Samarth Jurel exposes her ex Abhishek Kumar & his violence | Bigg Boss 17
By Bollywood Bubble| 157 views

Bigg Boss 17 WKW Update | Karan Kundra Ki Hogi Entry, Salman Ke Samne Dikhenge
#biggboss17 #salmankhan #karankundra
- Stay Tuned For More Bollywood News
☞ Check All Bollywood Latest Update on our Channel
☞ Subscribe to our Channel https://goo.gl/UerBDn
☞ Like us on Facebook https://goo.gl/7Q896J
☞ Follow us on Twitter https://goo.gl/AjQfa4
☞ Circle us on G+ https://goo.gl/57XqjC
☞ Follow us on Instagram https://goo.gl/x48yEy
Bigg Boss 17 WKW Update | Karan Kundra Ki Hogi Entry, Salman Ke Samne Dikhenge
By Bollywood Spy| 145 views

Tiger 3 Movie Gets 7 Am First Show On November 12
By Bollywood Crazies| 77 views

Soniya Bansal, the first contestant to get eliminated from Salman Khan’s Bigg Boss 17, recently sat down for a candid conversation with Bollywood Bubble host Rashita Sahni. The actress slammed Isha Malviya for sharing her bed with ex-boyfriend Abhishek Kumar despite being in a relationship with Samarth Jurel. She called out Mannara Chopra for using sisters Priyanka Chopra & Parineeti Chopra to get fame outside the BB house. Soniya also spoke about Munawar Faruqui’s inappropriate touch, Vicky Jain’s toxic behaviour towards wife Ankita Lokhande and Salman Khan’s biased behaviour on Weekend Ka Vaar. Watch the full interview here!
#soniyabansal #biggboss17
Check out the video to know more.
SUBSCRIBE To Bollywood Bubble:
Click Here ► http://bit.ly/2hjMB6X
Tune into Bollywood Bubble, your one stop destination for all the latest happenings, hot gossips, rumours and exclusive B-Town news...
Also, Visit - https://www.bollywoodbubble.com . One stop Destination for Latest Bollywood Updates.
Like us on Facebook - https://www.facebook.com/BollywoodBubble
Follow us on Twitter - https://twitter.com/bollybubble
Follow us on Instagram - https://www.instagram.com/bollywoodbubble/
Click on the Subscribe Button NOW and Stay Tuned.
Soniya Bansal slams Isha Malviya’s relationship with Abhishek-Samarth & Vicky Jain’s toxic behaviour
By Bollywood Bubble| 75 views